LDAP sync example
This is an example scenario of one-way LDAP entry synchronisation of selected user entries and attributes from a corporate directory (the source LDAP directory) to a SaaS provider directory (the target LDAP directory).
1. Initial target LDAP directory state
The target directory is set up with one branch per SaaS customer to receive the synced user entries. Each customer is also provided with a service account to login (for example via LDAP bind). The individual branches are isolated from one another by means of ACLs.
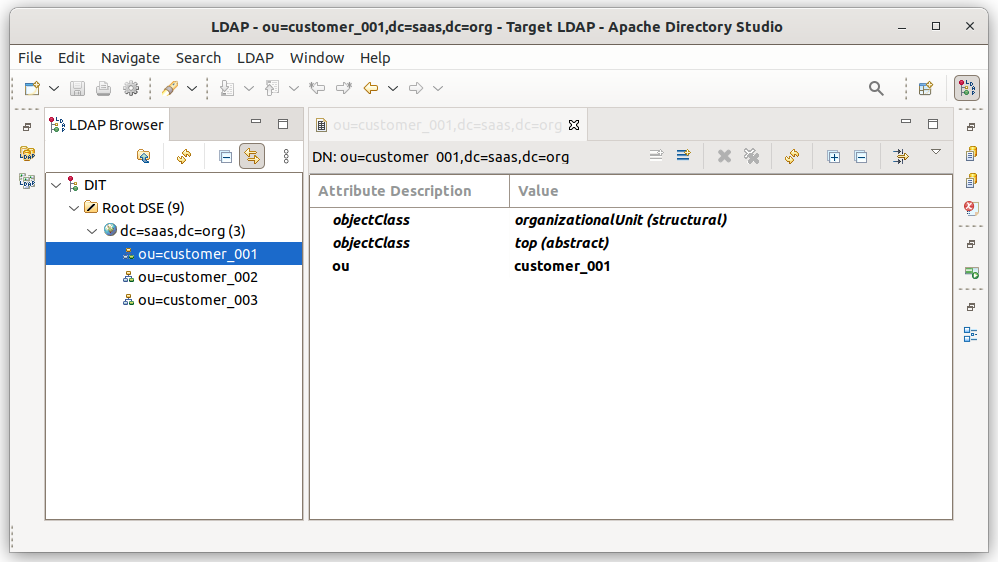
The target directory is located on the SaaS provider's premise or in the cloud and has a Json2Ldap web gateway for secure LdapSync agents access from the Internet.
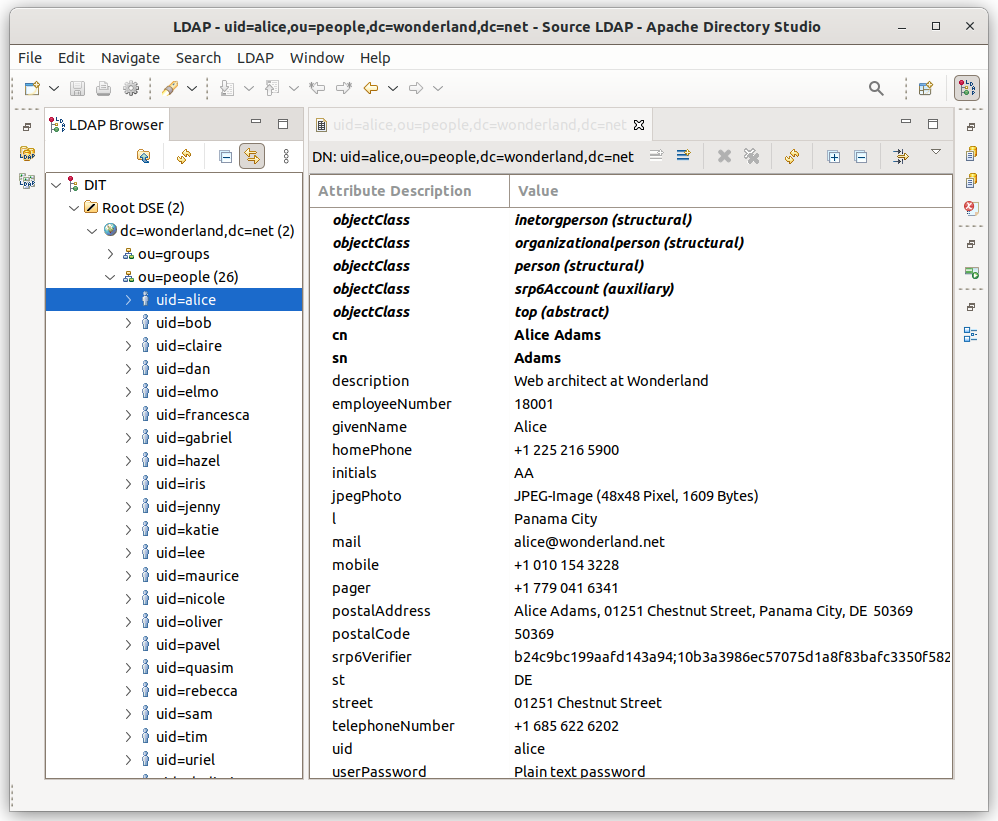
2. Source LDAP directory
The corporate LDAP directory has user entries placed under the
ou=people,dc=wonderland,dc=net DN.
3. LdapSync run performed
The SaaS subscriber is supplied with an LdapSync agent and the necessary credentials and config to sync selected user entries and attributes to the SaaS provider's LDAP directory.
The company admin configures the LdapSync agent with a standard LDAP search filter to determine which user accounts are to be synced:
sourceDirectory.search.baseDN=ou=people,dc=wonderland,dc=net
sourceDirectory.search.filter=(objectClass=person)
The admin also specifies which user attributes are to be synced (only those necessary for the SaaS operation) and whether any attribute name or value mapping should be done as well:
sync.attributeMap.uid=uid
sync.attributeMap.cn=cn
sync.attributeMap.sn=sn
sync.attributeMap.mail=mail
sync.attributeMap.mobile=mobile
sync.attributeMap.employeeNumber=employeeNumber;match=^(.*)$;replace=employee-$1
sync.attributeMap.jpegPhoto=jpegPhoto
The LdapSync agent is invoked periodically from a cron job. Example STDOUT output:
$ java -jar target/ldapsync.jar demo.properties
[ 2023-07-27 10:52:33 ] LDAP SyncAgent 1.9.1
[ 2023-07-27 10:52:33 ] Synchronisation will be performed once only (sync.period set to 0)
[ 2023-07-27 10:52:33 ] Attribute mapping: source directory -> target directory:
[ 2023-07-27 10:52:33 ] jpegPhoto -> jpegPhoto
[ 2023-07-27 10:52:33 ] uid -> uid
[ 2023-07-27 10:52:33 ] cn -> cn
[ 2023-07-27 10:52:33 ] employeeNumber [match=^(.*)$ replace=employee-$1 ] -> employeeNumber
[ 2023-07-27 10:52:33 ] mail -> mail
[ 2023-07-27 10:52:33 ] sn -> sn
[ 2023-07-27 10:52:33 ] mobile -> mobile
[ 2023-07-27 10:52:33 ] Starting synchronisation...
[ 2023-07-27 10:52:33 ] Connected to source directory at source.demo.c2id.com:10389 using transport security NONE
[ 2023-07-27 10:52:33 ] Authenticated to source directory as uid=ldapsync,ou=services,dc=wonderland,dc=net
[ 2023-07-27 10:52:33 ] Connected to remote Json2Ldap web service at https://demo.c2id.com/json2ldap/
[ 2023-07-27 10:52:33 ] Json2Ldap version: 3.6 (2023-07-04)
[ 2023-07-27 10:52:33 ] Connected to target directory with Json2Ldap CID loeeww78HlWSjkO95CLYbSqh58IwST3uES8w7MTtzgI
[ 2023-07-27 10:52:33 ] Authenticated to target directory as uid=customer_001,ou=customers,dc=saas,dc=org
[ 2023-07-27 10:52:33 ] Retrieved source directory entry uid=alice,ou=people,dc=wonderland,dc=net
[ 2023-07-27 10:52:33 ] Retrieved source directory entry uid=bob,ou=people,dc=wonderland,dc=net
[ 2023-07-27 10:52:33 ] Retrieved source directory entry uid=claire,ou=people,dc=wonderland,dc=net
[ 2023-07-27 10:52:33 ] Retrieved source directory entry uid=dan,ou=people,dc=wonderland,dc=net
...
[ 2023-07-27 10:52:33 ] Retrieved 26 matching entries from the source directory
[ 2023-07-27 10:52:33 ] Transformed source entry uid=alice,ou=people,dc=wonderland,dc=net employeeNumber attribute value: 18001 -> employee-18001
[ 2023-07-27 10:52:33 ] Transformed source entry uid=bob,ou=people,dc=wonderland,dc=net employeeNumber attribute value: 18002 -> employee-18002
[ 2023-07-27 10:52:33 ] Transformed source entry uid=claire,ou=people,dc=wonderland,dc=net employeeNumber attribute value: 18003 -> employee-18003
[ 2023-07-27 10:52:33 ] Transformed source entry uid=dan,ou=people,dc=wonderland,dc=net employeeNumber attribute value: 18004 -> employee-18004
...
[ 2023-07-27 10:52:33 ] Retrieved 0 matching entries from the target directory
[ 2023-07-27 10:52:33 ] Uploaded entry: uid=alice,ou=people,dc=wonderland,dc=net -> uid=alice,ou=customer_001,dc=saas,dc=org
[ 2023-07-27 10:52:33 ] Uploaded entry: uid=claire,ou=people,dc=wonderland,dc=net -> uid=claire,ou=customer_001,dc=saas,dc=org
[ 2023-07-27 10:52:33 ] Uploaded entry: uid=dan,ou=people,dc=wonderland,dc=net -> uid=dan,ou=customer_001,dc=saas,dc=org
[ 2023-07-27 10:52:33 ] Uploaded entry: uid=bob,ou=people,dc=wonderland,dc=net -> uid=bob,ou=customer_001,dc=saas,dc=org
...
[ 2023-07-27 10:52:33 ] Synchronisation complete: Uploaded entries: 26 Updated entries: 0 Deleted entries: 0
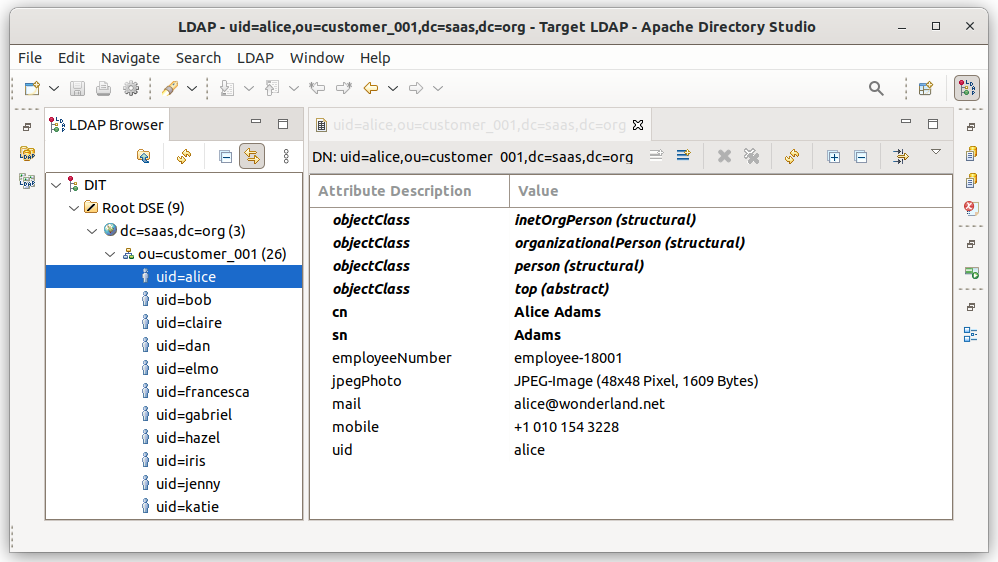
4. Target LDAP directory synced
After the LdapSync run the selected (and optionally transformed) user entries and attributes can be found in the customer's branch in the target LDAP directory.
The LdapSync agent is periodically invoked to sync any changes from the source to the target LDAP directory.
